Make your Windows XP Login Account Invisible!
Ok, If your parents have recently locked you out of their computer, then there is a way to make your account invisible, so they wont know that your account exists, and you can still logg in.
You have to edit your registry for this, so if you dont want to take the risk, then dont do it.
First off, you have to create your account.
1) Turn on computer and keep hitting F8 untill you are at the safe mode screen selection.
You have to edit your registry for this, so if you dont want to take the risk, then dont do it.
First off, you have to create your account.
1) Turn on computer and keep hitting F8 untill you are at the safe mode screen selection.
2) Logg in the administrator account, it shouldnt require a password, if it does, that means that your parents locked that account and you cant create you account.
3) If you are in, then go to control panel and create your account.
4) Restart your computer, and logg in your account. After everything is loaded, go to Start > Run > Regedit. The registry will popup.
Ok, now follow this root to make your account invisible.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\Cu rrentVersion\Winlogon\SpecialAccounts\UserList
Now right click, and go to New > DWord Value and name it YOUR EXACT USER NAME, like if your use name is JoE then nake it JoE, if its Joe, then name it Joe.
Now the value should be zero, if it isnt, the right click the value you just made and go to Modify, and make sure Value data is 0.
Now restart, and at the log in screen, you want see your username, now hit CTRL+
Now you have to do this everytime you wanna logg in. ( the CTRL+ALT+
Multiple OS Installation Guide
How to Use Newsgroups Guide
Introduction to Newsgroup Access
"Usenet" or Newsgroup access has been around since the beginning of the internet. Usenet was created to facilitate a central point of contact for discussion on a wide range of topics.
Many web sites employ several different techniques for feedback and discussion about content. Tons of "news" sites use forums for posting the latest and greatest content and allow their viewers to provide feedback. From using complicated forums to the basic PHP scripting that is required, anything can and will happen. Forums can come in many different flavors, including "basic" read and post to fancy boards with per user stats and custom "avatars" or icons. Most, if not all mail clients also can read and post usenet articles with little hassle.
As of this writing, I use Outlook Express 6, but most "newer" E-Mail clients have the same or similar type of features. In reality, the E-Mail or News client you chose could be much better than OE in many respects. I would love to use a more "feature rich" E-Mail client, but, sometimes I am rather hard set in my ways.
You also need to note two very important things:
- I DO NOT EVER display the "Preview Pane." This is a HUGE security issue.
- In OE 6, select View --> Layout --> Layout Tab --> uncheck "Show preview pane."
- I DO NOT view "HTML stationary" (or any other inlined images) as the sender intended. I view ALL E-Mail and Newsgroups as "plain text." This also reduces the chance of executing "malicious" HTML spam and makes for easier reading of high volumes of E-Mail and Newsgroups from many different people.
- In OE 6, select Tools --> Options --> Read Tab --> check "Read all messages in plain text."
1) Shall we begin? (Image 1.1) In Outlook Express 6.0, choose Tools --> Accounts... or you may select Set up a Newsgroups account... from the message pane. | ||||||||
2) Internet Accounts. (Image 1.2) | ||||||||
3) Internet Connection Wizard: Your Name. (Image 1.3) | ||||||||
4) Internet Connection Wizard: Your E-Mail Address. (Image 1.4) | ||||||||
5) Internet Connection Wizard: Your News Server. (Image 1.5) | ||||||||
6) Internet Connection Wizard: Finish. (Image 1.6) | ||||||||
7) Download Group Listing. (Image 1.7) | ||||||||
8) Newsgroup Subscriptions. (Image 1.8) |
9) Newsgroup Subscriptions. (Image 2.1)Which ever Newsgroup you subscribed to will now have an icon displayed next to it. You may now subscribe to additional Newsgroups or you can close the Newsgroup Subscriptions window by selecting Ok. |
10) New Post. (Image 2.2) |
11) New Post: Create Message. (Image 2.3) |
12) New Message. (Image 2.4) |
13) View all messages in group. (Image 2.5) |
14) View Posting. (Image 2.6) |
15) Reply to Group. (Image 2.7) |
16) Reply Message. (Image 2.8) |
Introduction
At some point in a computer operators lifetime, a need arises that many people do not even know is possible: Multiple OS's on a single computer.
Whether or not you:
- Require the extreme speed for gaming that, currently, only Win98 can offer.
- Desire the stability and enhanced memory management in Windows 2000 or XP.
- Wish to tinker with "the other guy's," such as Unix, Linux, or FreeBSD, just to name a few.
No matter what your need, Multiple OS's could fill that void.
Here, I put together an example of installing:
- Windows Me
- Windows XP Home
- Red Hat Linux
You may choose what ever combination desired, but, take note: Read your license agreement that came with your operating system to ensure that you are allowed a multi-boot environment.
A few points to consider before beginning the adventure:
- Decide what OS's you wish to install "before" beginning. This will avoid many headaches later on. Remember, if something gets messed up in the process, you could destroy all of your installs and hours of work. Planning is key to avoiding the simple, but disastrous mistakes.
- Plan out your partitioning scheme. With larger hard drives, it is best to have at least 10GB for each OS installation for drivers, etc. For this guide, I use very small partitions. Your results may vary:
- C:\ 1000 MB Windows 98
- D:\ 2000 MB Windows XP Home
- E:\ 4000 MB Red Hat Linux
- F:\ 2000 MB Shared Data
- G:\ 8000 MB Games
- Consider "how" to format each partition to ensure your requirements are met. For example, Windows 98 cannot read a partition formatted as NTFS, nor can Windows access a drive formatted with efs3 for Linux. As a result, the drive letters assigned may change due to the current OS not being able to read one or more of the partitions. To be on the safe side, it is always advisable to create a "shared" partition formatted with the "most common" file system to allow easy transfer between OS's. Currently, that system could be "FAT16."
- I ALWAYS install OS's in a very predictable order:
- DOS or other "early" OS.
- Windows 95, then 98, then Me. You could skip one or more.
- Windows 2000, then XP Home, then XP Pro. Again, you can skip one or more, depending on your requirements.
- "Other" OS's, such as Red Hat Linux, FreeBSD, or many others.
- Some "OEM" versions of Windows or "Recovery CD's" are not the full OS. With vast differences in these disks, I cannot predict if an "Upgrade" CD will detect your previous version properly, nor can I assume that "every" OS will be visible for you.
- Windows may "Upgrade" your previous installation if using an "upgrade" version of a newer OS. This is also is a factor when attempting to install another OS on the same partition. It is always best to split them up as described in step 2 and use "full versions."
- As a precaution, think steps 1 to 6 through again. :)
With the plan in hand, we can now begin:
At this point, if you are unaware of how FDISK works, please check my Using FDISK Guide.
If you are aware of how to partition your hard drives using FDISK, please continue.
For this Guide, I chose to install Windows XP Home as my "second" OS. I am not going to redo the complete guide here, but will touch on some important issues:
You can choose what ever OS Install Guide you wish, but I selected Red Hat Linux 7.2 next. As a result of that decision, the following technique was added to make things "easier."
Again, you can choose what ever OS Install Guide you wish, but my choice was Red Hat Linux.
Check out the Full Install Guide for Red Hat 8.0 because I am only going to hit on the high points with Red Hat 7.2 here:
I hope your Multi-Boot system works well for you!
E-Mail Filtering Guide
Introduction to E-mail Filtering
Spam and virus's has been a problem for many years but only until recently has people started to become disgusted with it. Performance could also be a concern for many people. One of those people is me. I do not like to use an additional program to combat something that should not be there from the start.
This guide explains how I fight spam and gives a few pointers as to what you can do without downloading an additional program. I also have included information on how to spot an E-Mail virus without any additional software. Only thing it takes is a little knowledge and the ability to refrain from opening every E-Mail you get, regardless of where it came from. What people do not understand is that the user must do something to get a virus. It is not magic. That something, a very high percentage of the time, is click and open an infected E-Mail. DO NOT DO THIS!
Something to consider is the fact that the E-Mail filters and spam filtering do NOT work with HTTP E-Mail accounts, such as Hotmail and Yahoo. Most of those kind of services offer filtering of their own. Use it.
This guide also offers a sneak peek inside Black Viper's inbox.
As of this writing, I use Outlook Express 6, but most "newer" E-Mail clients have the same or similar type of features. In reality, the E-Mail client you chose could be much better than OE in many respects. I would love to use a more "feature rich" E-Mail client, but, sometimes I am rather hard set in my ways.
You also need to note two very important things:
- I DO NOT EVER display the "Preview Pane." This is a HUGE security issue.
- In OE 6, select View --> Layout --> Layout Tab --> uncheck Show preview pane.
- In Outlook 2002, select View --> Preview Pane (toggle: select to disable, select to enable)
- In Outlook 2003, select View --> Reading Pane --> select Off
- I DO NOT view "HTML stationary" (or any other inlined images) as the sender intended. I view ALL E-Mail as "plain text." This also reduces the chance of executing "malicious" HTML spam and makes for easier reading of high volumes of E-Mail from many different people.
- In OE 6, select Tools --> Options --> Read Tab --> check Read all messages in plain text. (Option available with IE6 SP1 installed).
- In Outlook 2002, you must download the latest service pack and add a setting in the registry. Instructions on how to do this is here: http://support.microsoft.com/default.aspx?scid=kb;en-us;307594
- Ensure you have the latest service pack already installed and you can download and apply this registry patch: Outlook2002PlainTextFix.zip ~ 330 bytes
- In Outlook 2003, select Tools --> Options --> Preferences Tab --> E-mail options... button --> check Read all standard mail in plain text.
The other day I came across a clients computer that was getting the infamous Blue Screen of Death (aka BSOD). However, since the computer had the “Automatically Restart if the event of a bluescreen” option switched on, the system would restart and the blue screen disappear too quickly for me to read. Most technicians will just go into Safe Mode and switch this off, but what if you cant get into Safe Mode? What happens if the option to “Disable Automatic Restart” doesn’t show in the F8 menu either?
I had this happen to me and I found a way around it. Read on.
For those of you who aren’t familiar with the blue screen of death. It is a screen that shows up when Windows has a critical failure. It has messages of what went wrong with the computer and can greatly help technicians figure out what is causing the error.
Anyway, most of the time this “automatically restart” option isn’t a problem for computer technicians because we can just log into Windows Safe Mode (F8) and turn it off by doing the following:
Right Click on “My Computer” and goto “Properties”. Then goto the “Advanced” tab and under the headline “Startup and Recovery”, press the “Settings” button. Untick the “Automatically Restart” box and press Ok.
However, in this instance Safe Mode wouldn’t start up either. In most cases if you press F8 after a BSOD crash you will have the option “Disable Automatic Restart”. I wasn’t getting that either. So here is my way to turn off Automatic Restart.
Note: You will need access to a working computer to do these steps. You will also need a fairly good knowledge of computers, BIOS and registry editing in order to do this. This article is aimed towards computer technicians.
1. If you don’t have it already, download UBCD4Win using one of the mirrors here. To run it, create an ISO and burn it to CD you can read the instructions here. I wont write the instructions here because the ones on the previous link are better and this article is more targeted at computer technicians and most of them already have this CD.
2. Once the CD has been created, goto the BIOS and make sure your CDRom is set as the first boot device. Start up the computer with UBCD4Win in the CDRom and you will have some boot options. Choose the “Launch The Ultimate Boot CD for Windows” option.
It will take a few minutes to load fully, but when it does you should see a Windows XP like interface like in the picture below:
3. In the UBCD4Win interface, goto Start > Programs > Registry Tools > RegEdit(Remote)
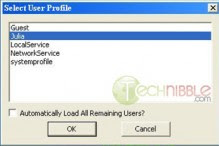
4. The program will then ask “Do you wish to load remote user profile(s) for scanning?”. Choose Yes.
5. It will then ask you to “Select User Profile”. Choose the main user account. It may be “Administrator” or some other username (but not Local Service, NetworkService or systemprofile). In the instance of the screenshot below, its “Julia”.
6. Now you should see a Window named “Registry Editor” which is identical to the usual “regedit” under Windows. Navigate to the following key:
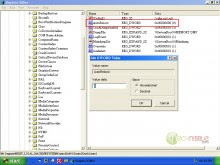
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\CrashControl
7. In here you will find a key named “AutoReboot”. Double click on it to edit its DWORD Value and under “Value Data:” the current value should be 1, which means AutoReboot is turned on. Change this to 0 (which turns it off) and press OK.
8. Restart the machine and try and boot into the normal Windows mode. You should now see the blue screen of death. Write down the “STOP:” number and the error message. You can look for the solution up using Google or check out our article on common blue screen error messages.
Join N/A other readers and subscribe to Technibbles Email Digest and receive new posts sent directly to your inbox. All new signups get a copy of our Computer Technicians Quick Reference Guide free. Signup Now!
Sometimes we will set the window password to prevent other people using it but how about if you forgot the setting password? here i show you how to access and log in to your computer
Step 1 - After power on your computer (before window logo appear), then press F8 key access to safe mode and select safe mode with command prompt.
Step 2 - After entered into window, selected the 'administrator' account and it will show up command prompt.
Step 3 - Now we use 'Net' command to add another window user, for example add a user name jet, key in net user jet /add into command prompt.
Step 4 - Upgraded new user to administrator level, net local group administrators jet /add key in into command prompt.
Step 5 - Press Ctrl+Alt+Delete, select 'shutdown' -> 'restart'.
Step 6 - After restart, the window will appear new user,
If your 'administrator' account already set up the password, the method that mentioned above can't be use.
Forgot Your Window Password?